iPhone Security: Apple Refuses FBI's Demands to Create iOS Backdoor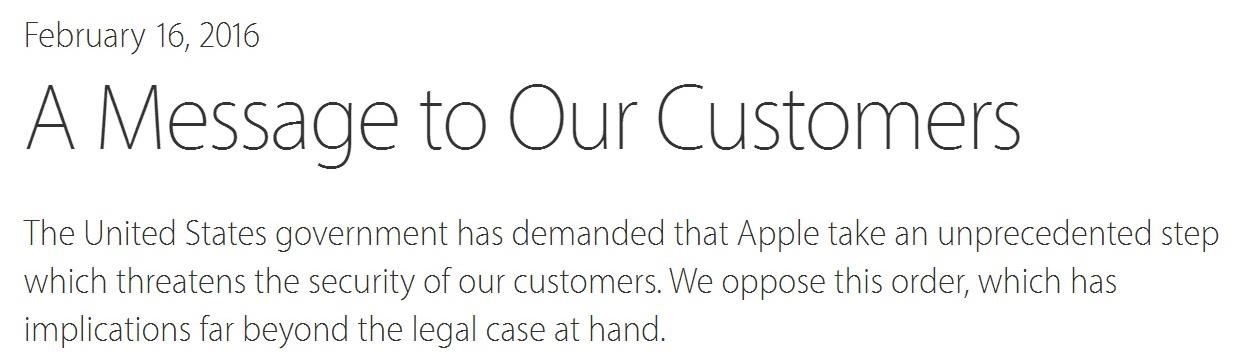
In a letter dated February 16th, Apple CEO Tim Cook responded to the FBI's demand that Apple create a "backdoor" to bypass the encryption on an iPhone used by one of the perpetrators of last year's terrorist attack in San Bernardino, CA. Cook began the letter by stating that Apple has "no sympathy for terrorists" and has cooperated in giving the FBI all of the information that it has available.However, Cook says that Apple itself does not have technology that could bypass iOS encryption, and that creating such a backdoor has the potential to compromise the security of all iOS users, and is not a step the company is willing to take.The U.S. government claims that it's only interested in the bypass for this specific phone—a work phone used by Syed Rizwan Farook—and not any others, which, uh... well, you all know what laughter sounds like.
Information in the Government's HandsEven if the government has no honest intentions of using an iOS backdoor for nefarious purposes, it's pretty hard to believe that such sensitive material wouldn't wind up in the wrong hands—especially considering its history keeping track of laptops with classified information, firearms, and nuclear weapons.You also have to wonder if there's even anything important on Farook's work iPhone. Farook and his wife/accomplice, Tashfeen Malik, destroyed their personal phones to the point that any data was unrecoverable, and a hard drive from the couple's computer is still missing. Sure, it's possible that there's evidence on the work iPhone, but the odds seem low considering the steps these two went through to destroy other evidence.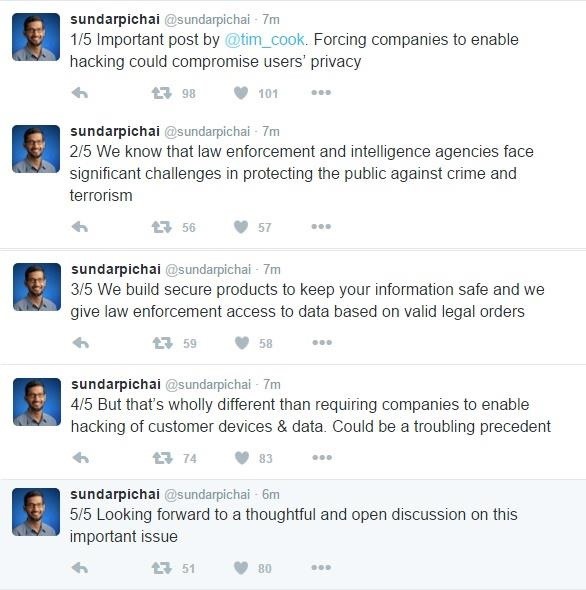
What's the FBI After?What the FBI is demanding is basically an override of iOS's passcode encryption. Currently, the system will wipe all data off the phone after 10 consecutive incorrect entries. The FBI wants this fail-safe removed so that it can enter passcodes electronically and at high speeds, to "make it easier to unlock an iPhone by 'brute force,' trying thousands or millions of combinations with the speed of a modern computer," said Cook.Once the encryption is breached, the FBI could access an iPhone, and the "government could extend this breach of privacy and demand that Apple build surveillance software to intercept your messages, access your health records or financial data, track your location, or even access your phone's microphone or camera without your knowledge," Cook writes. Given its track record, there's basically no way to believe that the United States government wouldn't meddle with such powerful technology.On the other hand, you can argue that having remote access to smartphones would come in handy when trying to snuff out potential terror threats. But considering the attention this is receiving, you'd be stupid to think that terrorists, or anyone else with malicious intentions, would continue using smartphones at all, knowing that law enforcement could be watching them at any or every moment.You'll probably hear some noise about how Tim Cook and Apple are enabling terrorists by refusing the FBI's demands, but that's going too far. If you want to get cynical about it, Cook's statement is as much about principle as it is about retaining Apple's customer base (and maybe even using this protest win new customers).But Cook's outlook is correct. The government's argument is paradoxical—it demands that we relinquish our security, so that we may be more secure. Hopefully the other tech giants (I'm looking at you Google) join in the fight to protect our data.UpdateSundar Pichai, CEO of Alphbet's Google, has chimed in (though we were hoping for more). But I suppose another post from another big tech CEO isn't going to move the narrative along all that much.Let us know what you think... Is the government extending its reach too far? Is Apple in the wrong for not complying? Sound off below.
Cover image via Shutterstock
Below are detailed instructions on how to loan a Kindle ebook to a friend or family member, as well as instructions on how they can then download the shared Kindle book to their device. Be sure to read the "Lending Limitations" section below so you know what you can and can't do when loaning out your Kindle books.
How to Share Amazon Kindle Ebooks | CIO
Activate Hound Without an Activation Code on Android [How-To] Papi. năm ngoái | 0 lượt xem. Báo cáo. Duyệt thêm video. Đang phát tiếp theo. 3:23.
I Phone 5c Bypass Activation Code? Possible? iOS8 « iOS
The Ultimate Facebook Prank : How To "Kill" Your Friends on Facebook by Faking Their Deaths It only takes a minute for something well intentioned to turn into something sinister. Facebook created 'memorial pages' as way for friends and family to share their thoughts and feelings for those that are no longer with us.
How to Fake your death online « Practical Jokes & Pranks
PUBG Mobile will lag on your phone if its cache is cluttered. You simply need to clear the cache of your phone and restart it to fix a minor lag in your game. Here is how to do so. Samsung Galaxy users can turn off their phone and then turn it on by using Volume Up + Home + Power button or Volume Up + Bixby + Power button.
गैलेक्सी S6 या नोट 4 पर गेम्स के लिए Lag & Boost का प्रदर्शन
How do I enable the classic view or classic shell in windows 10? I seem to remember reading ahead of time that there would be a way to make windows 10 look and function much more like windows 7 which is why I was looking forward to this upgrade. However I cannot find the controls to do this.
Volume Controllers Sold Direct on eBay | Fantastic Prices on Volume Controllers
AD
This tutorial discusses how to group Live Tiles in Windows 10.The introduction of Windows 8 marked the beginning of an entirely new and radically different UI design philosophy for the Windows line of Operating Systems.
How to Tweak Your Tiles in Windows 10 | PCMag.com
We've all been in a similar situation before—you set your phone's ringer to silent before heading into class, and when you check your phone hours later, you find that your silenced phone didn't alert you to 8 missed calls and 17 text messages. Well, I don't actually get that many texts or calls in real life, but I'm sure some of you do.
How do I use text messages on my device? - samsung.com
Boost Camera Resolution & Photo Quality on Your OnePlus 5 or
Also, with CMTE, it was essential for the user to reboot their device, whereas upon using full Substratum mode, one can dynamically theme their device without the need to reboot. Furthermore, CMTE as a project has been left out ever since Android Nougat, while Substratum's development continues to grow.
How to Theme your Android Device With Substratum
The Nook Color is a $250 e-reader powered by Android. Learn how to hack it into a powerful and fully functional Android tablet. The Android Honeycomb 3.0 operating system and the first fleet of
How to Turn Your NOOK Color Into an Android Tablet
how you can eliminate bloatware on your Samsung Galaxy Note 8 smartphone. I hope this method will be helpful to Remove Bloatware from Samsung Galaxy Note 8.
Uninstall All Bloatware On Samsung Note 4 - techjunkie.com
0 comments:
Post a Comment